Sentry Detect: Managed Detection Engineering
Close exposed detection gaps
Our continuously curated, behavior-based detections are custom-built for your Microsoft Defender XDR and Sentinel environments—reducing false positives and enabling confident, proactive defense upscaling of your team.
We help SOC teams staying ahead of advanced threats.
Together, we defend your organization
Sentry Detect integrates with your Microsoft Security platforms
Defender XDRMicrosoft
SentinelMicrosoft
AzureMicrosoft
600+ premium high-fidelity detections
for SOC teams in: Finance, Insurance, Energy, Manufacturing & Retail
Introducing Sentry Detect
Close detection gaps now
High-fidelity, behavior-based detections
- Curated detection library
Access 600+ detections developed by our engineers and red team specialists, focused on advanced threat actor behavior, not on signatures
- Complete implementation support
We integrate, tune, and maintain detections within your environment (single or multi-tenant)
- Full documentation per detection
KQL queries, implementation guides, MITRE ATT&CK mapping, and threat context
Advance team capabilities
Supporting toolkit and expertise
- Sentry web portal
Review, prioritize and select detections
- Detection-as-code pipelines
Efficiently manage and deploy custom detections
- Risk-based scoring engine
Identify high-risk issues based on correlated events
- Access specialist expertise
Regular meetings with FalconForce specialists to refine and improve detection strategies
Pricing
Starter pack or Pro plan
- Starter pack
Get going with a one-time implementation of a fixed number of detections
- Pro plan
Go pro with continuous delivery and tuning via detection-as-code practices
Start with our Sentry Detect portal
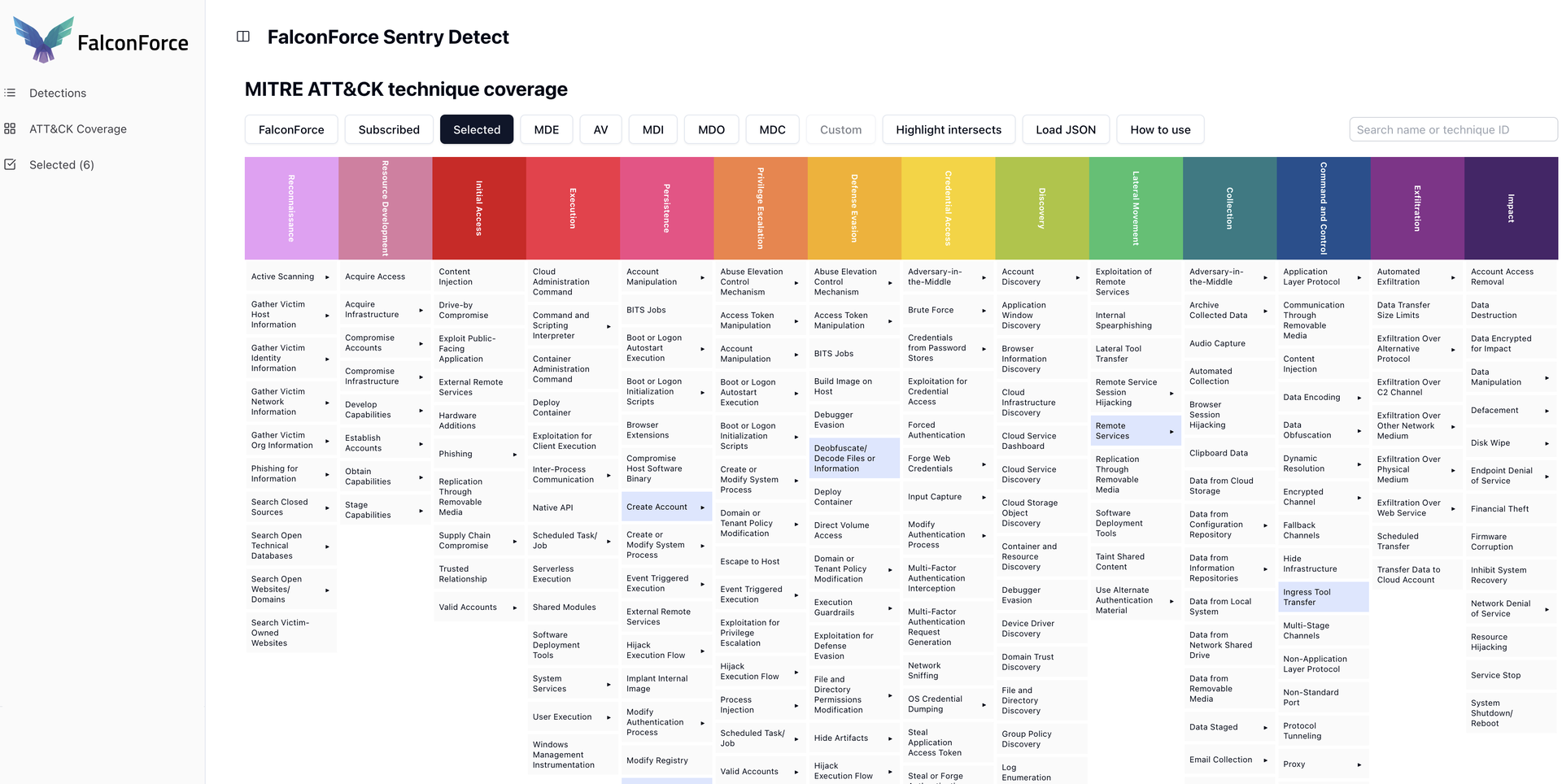
We start where off-the-shelf detections underperform
How Sentry Detect supports your SOC
Discover and close gaps
We help you identify which critical adversary techniques your current detections miss, then provide the specific coverage needed to address those blind spots systematically.
Reduce operational burden
By implementing and maintaining high-fidelity detections in your environment, we free your team from building detections from scratch and managing false positives, allowing them to focus on investigation and response.
Accelerate capability development
Your team gains practical detection engineering knowledge through working with our experts and production-ready detections, building internal expertise whilst improving your security posture.
Interested? Request access below
6 steps to enhance your threat detection
Build the foundation
Set up access to your environment for the FalconForce team. We implement detection-as-code pipelines and the risk-based scoring engine.
Set the roadmap
Together, we draft a roadmap for detection implementation, based on known detection gaps and FalconForce input.
Tune detections
FalconForce professionals use the pipelines to deploy and tune the selected detections in your environment.
Validate detections
The detections run for some weeks to validate that tuning is effective. Where needed, re-tuning is performed.
Move to production
The detections go into production, alerting your SOC team for advanced threat actor behavior. You can use the risk-based scoring engine for additional insights.
Perform maintenance
In close consultation with your team, minor and major updates are made to the detection logic and documentation.
FalconForce tools for your SOC
1. Sentry Detect web portal
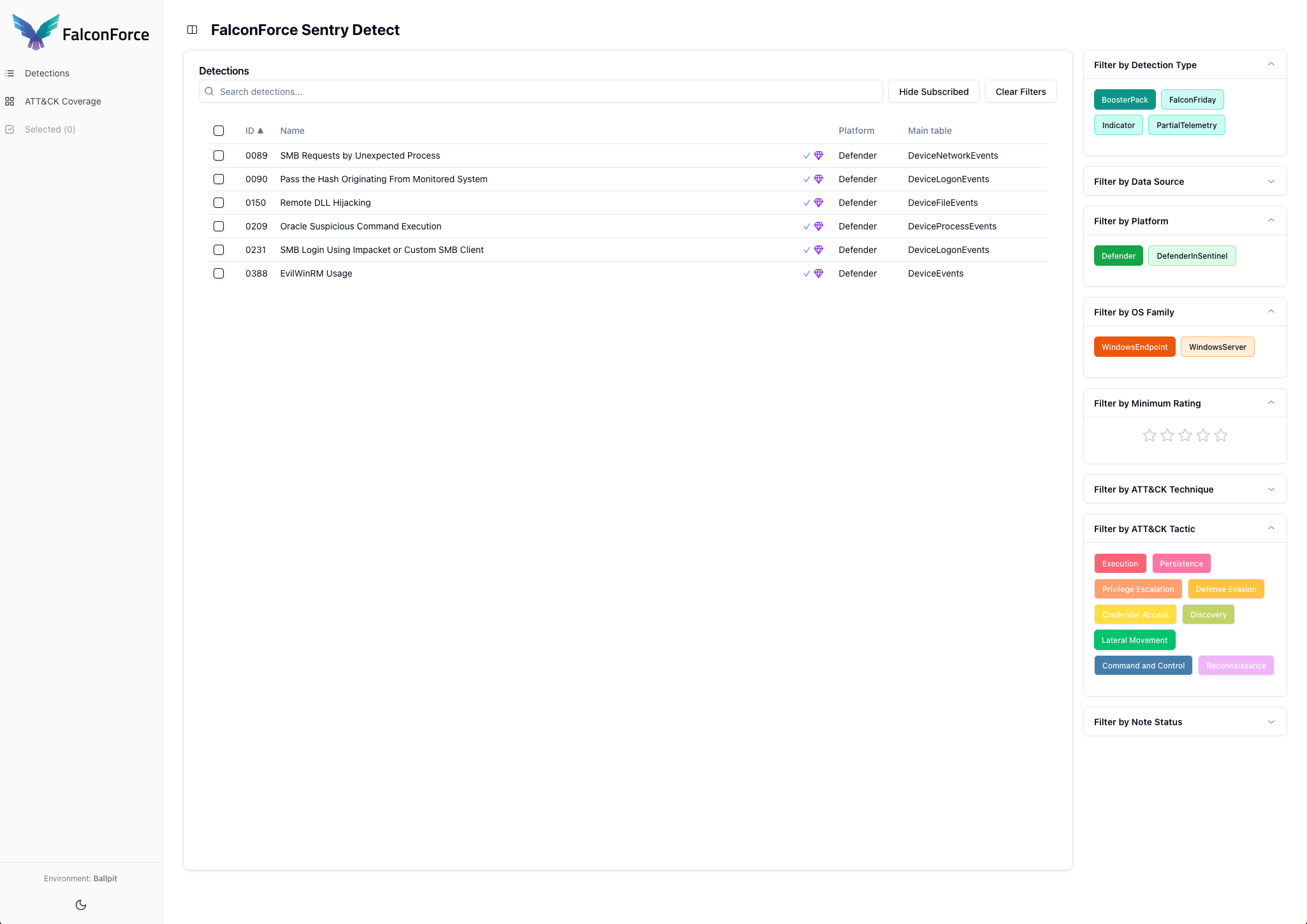
Search our complete detection repository. Access meta data of individual detections to learn more. Mark and annotate the detections you are interested in.
2. Detection-as-code pipelines
The pipelines follow CI/CD principles. This includes automated (syntax) validations on all files, KQL queries and detection definitions.
3. Risk-based scoring
Analyze and correlate alert (meta) data. Identify related events. Your analysts identify high-risk events that would otherwise go unnoticed.
Trusted partnership with our clients
FalconForce’s advanced detection content has greatly boosted our detective capability in both breadth and depth. The steady stream of new, tuned and well-documented detections and discussions with FalconForce’s experts really enhance the efficiency of our team.
Simon – Head of information security & risk management @Athora
Bespoke detection content explained
Watch our webinar about Sentry Detect facilitated by Olaf (Detection Engineer) and Henri (Offensive Defender).
Discover how we architected and deliver Managed Detection Engineering services.
Our vision on modern detection excellence
Pro-active capabilities
Move your protective detection and protection capabilities beyond signatures. Understand attacker behavior and develop solid, well-documented detections for these attacks.
Systemic coverage
Pursue systematic detection coverage against globally recognized frameworks (such as MITRE ATT&CK). Focus on the threats that matter for your business.
Operational excellence
Balance smart automations (of repetitive tasks) with human knowledge & expertise to focus on managing advanced threats. Leading to a mature detection capability.
High-fidelity detections
Ensure consistent, high-fidelity, custom detections, covering sophisticated threat actor behavior.
We are happy to meet you and discuss how we can help. Please reach out to Givan to start a conversation!
Email: [email protected]
Phone: (+31) 85 044 93 34
Frequently asked questions
How do we (SOC teams) get the most out of your detections?
Together, we select detections that are most relevant to threats your company faces or detection gaps known. Our detections flag a wide variety of attacker behavior, instead of relying on specific IoCs (such as hashes or ip addresses). This makes our detections more reliable in case the threat actor changes their toolkit or location. The threat actor behavior we identify is based on our red teaming experience in the field, own R&D and real-life incidents.
Do the detections come with documentation?
Yes, each detection comes with documentation, including tagging relevant MITRE Tactics / Techniques, used data sources, a (technical) description, known blind spots or false positives, considerations, a brief response plan and references to useful external information resources.
On which SIEM platforms do your detections operate?
Our detections have been specifically designed for the Microsoft Sentinel and Defender XDR platforms. We make the most out of the powerful KQL query language and have extensive experience with the Microsoft stack.
How does your Sentry Detect service integrate with our existing security stack?
Our detection content and tooling will be embedded in your Sentinel and Defender XDR stack. Your team will collaborate with our seasoned experts to deploy and tune our content, and enhance overall efficiency in your detection lifecycle management.
Do you support detections-as-code with Sentry Detect?
Yes, our detections are fully set up as detections-as-code. We also include pipelines (in DevOps, GitHub or GitLab) to support you in managing the lifecycle of our (and your own-developed) detections.
Do we get updates / maintenance on your detection content?
Yes, in case you have a Sentry Detect Pro plan, we make updates to our detection content available to you, and we can support implementing these updates into your environment. We will also inform you in case we decide to deprecate detections. For example, in case the threat actor behavior is now detected by an out-of-the-box Defender rule.
How many detections are in your current repository? What data sources and platforms are covered?
Currently, we have about 600 premium detections in our repository. These detections cover a variety of data sources and platforms, including Azure, MDE, and Linux/Mac. You can see the meta data of all these detections via our web portal. For example, to look at our detections that use the data sources relevant to your organization and select these.
When & how often does our SOC team engage with the FalconForce team?
We jointly decide on a communication channel to stay in touch and stimulate interaction. An update meeting is held at least 1x month.
Will this overload my SOC analysts with yet another stream of alerts, especially when we’re already overwhelmed?
We support you in tuning our detections to your environment, to reduce false-positives.
How can our SOC team get started with FalconForce?
Contact us today to discuss your cybersecurity needs and request a demo call with Givan.
Energieweg 3
3542 DZ Utrecht
The Netherlands
FalconForce B.V.
[email protected]
(+31) 85 044 93 34
KVK 76682307
BTW NL860745314B01

