I honestly can’t take credit any for any of this though, it has all been created by some well respected friends. SadProcessor has created a couple of great PowerShell modules that amongst a lot of other features allows you to add the MITRE ATT&CK dataset to Neo4j, which in turn can then be visualised by Bloodhound.
Bloodhound is created and maintained by Andy Robbins and Rohan Vazarkar. It is an amazing asset for defenders and attackers to visualise attack paths in Active Directory. If you’ve never used it set apart some time to do so. It really is a powerful tool to understand and improve your defensive posture.
However, in this case we’ll borrow the great GUI to visualise the relationships between objects in the ATT&CK framework.
Bear in mind (no pun intended) the implementation albeit far from perfect, with some effort can certainly be a lot more polished but it is quite usable as it is.
Neo4j
One of the pre-requisites is that you have a Neo4j instance running. You can get the community release for your preferred operating system here.
After setting it up you need to make one change to the configuration to allow the later discussed PowerShell module to be able to connect.
Now you need to modify conf/neo4j.conf. and remove the # before the dbms.security.auth_enabled rule to disable auth
# Whether requests to Neo4j are authenticated. # To disable authentication, uncomment this line dbms.security.auth_enabled=false
PowerShell modules
You need a PowerShell Core install, this works on Windows, OS X or in my case a Linux Kali box (because I don’t want JVM on my workbox).
In order to get the data into Neo4j we will be using two modules and a script: ATTCKnowledge.ps1, an older version of CypherDog and finally the PushToBh.ps1
Download these three scripts, or clone the whole repo. Next execute a fairly simple set of commands;
. ./CypherDog15_Alpha3.ps1
. ./ATTCKnowledge.ps1
./PushToBH.ps1
Make sure you add the dots as well, otherwise it will not work.
You’ll be greeted with some sweet ASCII art and a bunch of errors, depending on the OS but on all my systems the result was fine so I honestly never bothered to look into them.
BloodHound
Next it’s time to fire up BloodHound and connect it to the Neo4j database. Even though you disabled authentication the BloodHound client still requires you to enter some credentials so just type anything you want, it doesn’t matter.
Once we’re in we can start querying the data. Neo4j uses the Cypher Query Language, which took me a bit of getting used to. Special thanks to Andy Robbins for helping me with some of the Cypher queries. The Bloodhound Slack is a great place to hang out and learn. Additionally there are quite some good resources out there, one of which again by SadProcessor.
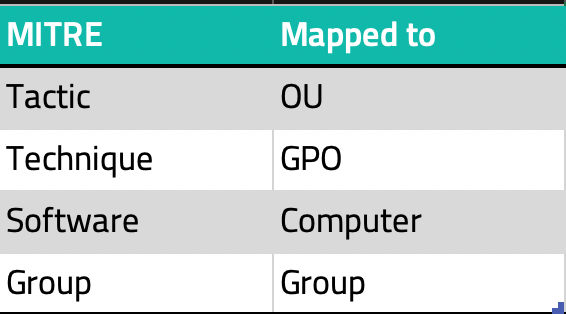
In the original PushToBh script some of the field names have been remapped to what BloodHound expects, keep this in mind when querying.
You can change these names to the original names before pushing it to the database.
The only difference will probably be that all icons will look the same.
Let‘s say I’m interested in what techniques Russian actors are using. One way of doing this could be by searching for all techniques that have a relation to an actor group that has Russia in their description. This will result in the following query:
MATCH a=((G:Group)-[r:Uses*1]->(O:GPO)) WHERE ToUpper(G.Description) CONTAINS "RUSSIA" RETURN a
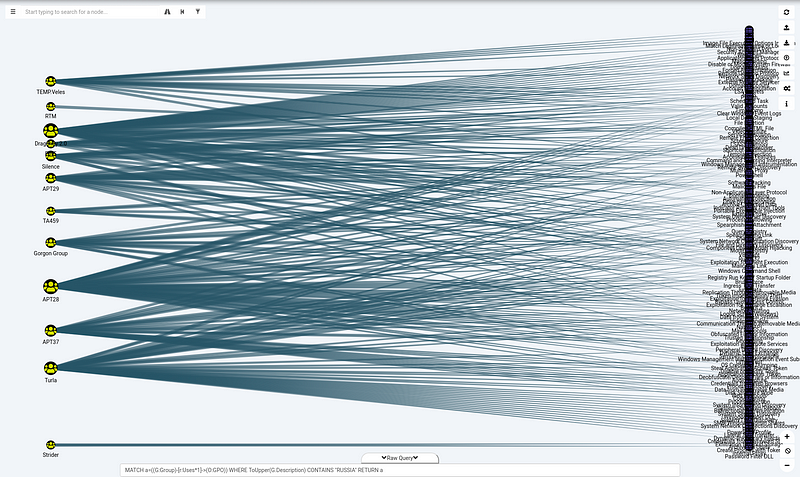
Apart from too many results to properly read it there is another issue with this query. It can also contain groups that might have targeted Russia instead of originating from there.
After some threat intelligence effort you probably have been pointed to some Dukes and some Bears so a more focussed query could be:
UNWIND ['APT27','APT29','Turla'] as DukingBears MATCH (G:Group) WHERE G.name CONTAINS DukingBears MATCH a=((G:Group)-[r:Uses*1]->(O:GPO)) RETURN a
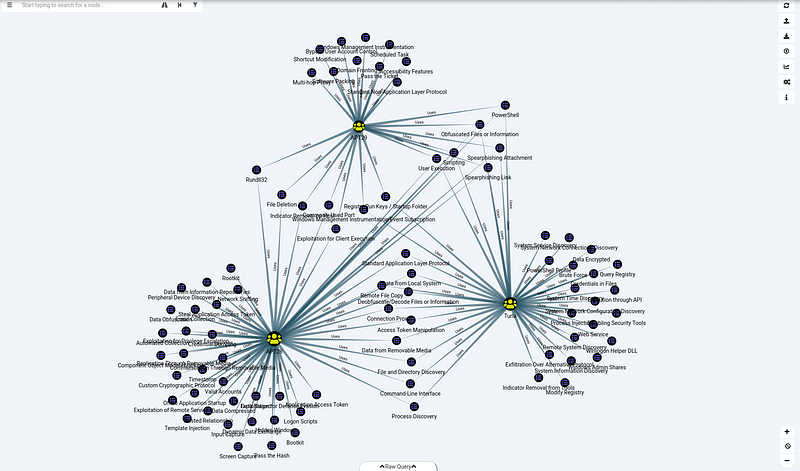
As you might have spotted there are a few techniques in the middle of the screenshot that have relations to multiple groups. These might be the most interesting to investigate first to start building detections.
Should you be interested in which techniques out of all these girls or guys have been observed to be using and are also used by others and who? You could have a look at this query:
UNWIND ['APT27','APT29','Turla'] as DukingBears MATCH a=((G:Group)-[r:Uses*1]->(O:GPO)) WHERE G.name CONTAINS DukingBears WITH O as techniques MATCH b=((G2:Group)-[r2:Uses*1]->(techniques)) RETURN b
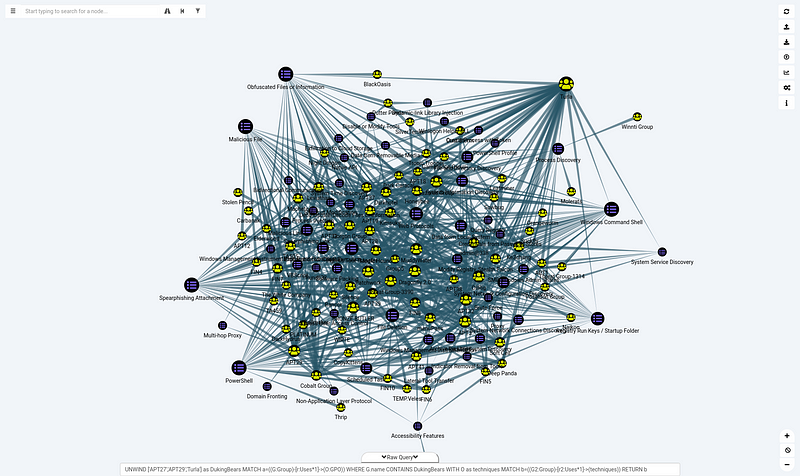
Again this is clearly too much information, lets first have a look at some that stand out. I’ve picked the following techniques: PowerShell, Windows Command Shell and Obfuscated Files or Information. This query is fairly simple:
MATCH a=((G:Group)-[r:Uses*1]->(O:GPO {name:'PowerShell'}))
MATCH b=((G1:Group)-[r1:Uses*1]->(O1:GPO {name:'Obfuscated Files or Information'}))
MATCH c=((G2:Group)-[r2:Uses*1]->(O2:GPO {name:'Windows Command Shell'}))
RETURN a,b,c
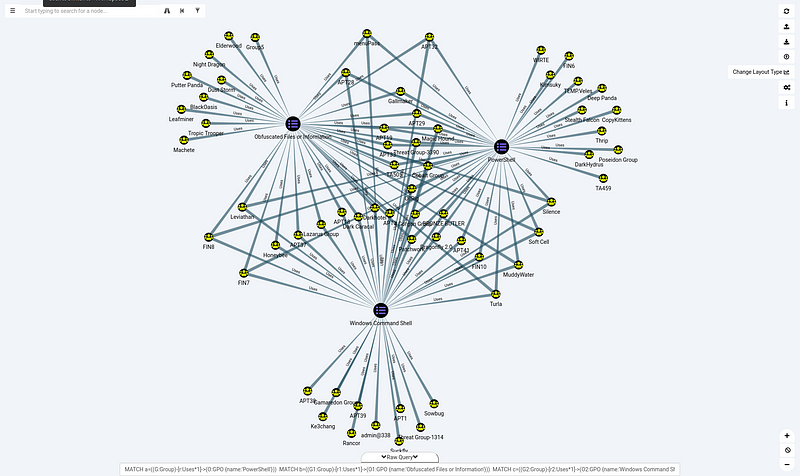
Interestingly many actor groups pop up. There are even a few of them that also use all three techniques, so investing some time to protect and build detections agains these aught to be time well spent.
Wrapping up
This is potentially interesting information to talk about with your threat intel colleague(s). Obviously ATT&CK is never complete and next to a delay of several months it also heavily relies on public reports. All these factors might have changed so some of these groups might be shifting targets or using different techniques already.
The reliance on public reporting also adds several gaps, since not everything is in a report and there is a certain risk of biases. Use your own critical rationale and don’t use this as your single source of truth.
Knowledge center
Other articles
Why is no one talking about maintenance in detection engineering?
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
dAWShund – framework to put a leash on naughty AWS permissions
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Exploring WinRM plugins for lateral movement
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Together. Secure. Today.
Stay in the loop and sign up to our newsletter

FalconForce realizes ambitions by working closely with its customers in a methodical manner, improving their security in the digital domain.
Energieweg 3
3542 DZ Utrecht
The Netherlands
FalconForce B.V.
[email protected]
(+31) 85 044 93 34
KVK 76682307
BTW NL860745314B01