Sysmon 11.1 has been released, almost a month after the release of version 11.0
Unofficial release notes :
- On some Windows builds the ProcessCreation events (EventID 1) were not created, this has been resolved
- Updated file stream hash event to capture the contents of text streams < 1KB, with the goal of capturing Mark Of The Web i(MOTW) streams.
- To accommodate this new field, the schema has been updated to 4.31, check it out here
- The -a command-line option has been removed. To set a custom archive directory the configuration option has to be used in the root section of the configuration file.
<ArchiveDirectory>FalconForce</ArchiveDirectory>
- Fixed a bug that restored read-only files to the same directory, irrelevant of the FileDelete configuration.
Mark pointed out that he wants to limit the command-line options in favour of configuration parameters, which I appreciate. It’s a lot easier to maintain it this way, especially in an enterprise environment.
New: Mark Of The Web capture
Each downloaded file is is tagged with a hidden NTFS Alternate Data Stream file named Zone.Identifier.
You can check for the presence of this “Mark of the Web” (MotW) using dir /r or programmatically, and you can view the contents of the MotW stream using Notepad:
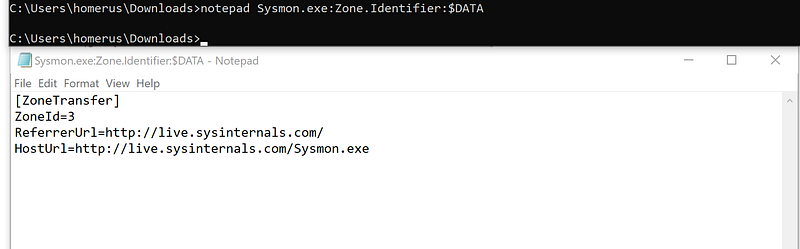
This data will now also be captured by Sysmon in the FileStreamHash event (EventID 15) in the Contents field.
Please note that you will see 3–6 events per downloaded file. This is due to the behaviour of urlmon.dll, the library responsible for downloading files via HTTP. This opens and closes the stream multiple times to append MOTW information.
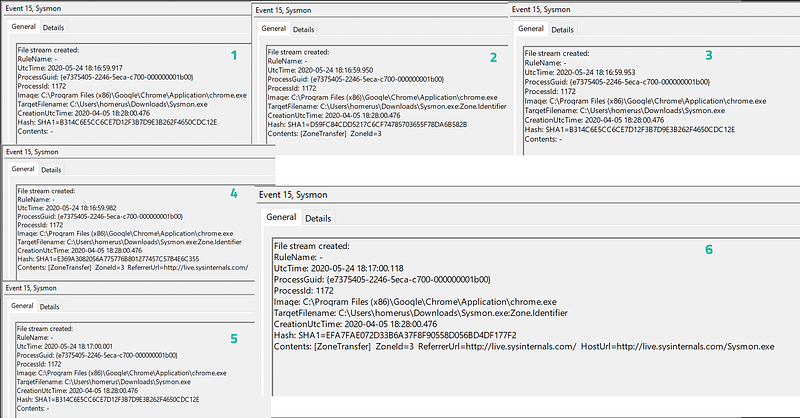
This feature is enabled by default and cannot be configured specifically. Once you enable the FileStreamHash event (EventID 15) for certain directories it will be included from there on out.
So What?
So you can see URLs for a downloaded file, is this useful? Why yes, most certainly. This will make triage in a lot of cases a lot more straight forward since you now have a clear source of the malicious file.
I’ve demonstrated it above with a PE file but the same is valid for other file types, like word documents and so on.
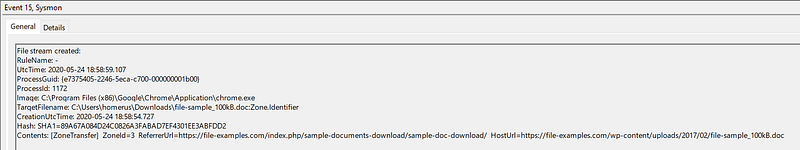
It would make sense to at least point this at the Downloads folder of a user and possibly some additional folders, like the office download folders and so on.
Knowledge center
Other articles
Why is no one talking about maintenance in detection engineering?
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
dAWShund – framework to put a leash on naughty AWS permissions
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Exploring WinRM plugins for lateral movement
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Together. Secure. Today.
Stay in the loop and sign up to our newsletter

FalconForce realizes ambitions by working closely with its customers in a methodical manner, improving their security in the digital domain.
Energieweg 3
3542 DZ Utrecht
The Netherlands
FalconForce B.V.
[email protected]
(+31) 85 044 93 34
KVK 76682307
BTW NL860745314B01




