I’ve been a huge fan of MITREs ATT&CK framework ever since its release. It has been of enormous value to the whole InfoSec community and it will hopefully continue to remain so for a long long time.
We’re on the verge of one of the biggest overhauls since its release, the introduction of sub-techniques, or when you read this they might be out already. I personally believe this is a great step forward. This introduction will cause everyone to do a big overhaul of their detection tagging and improvement of their ruleset.
On the positive side it will also bring a lot more clarity and granularity and it will bring more insight to a lot of people of possible attack techniques they weren’t aware of before.
As some of you know I’m quite a visual person and one of my projects is a Splunk application for ThreatHunting which is heavily ATT&CK focussed.
I’ve been building some new dashboard visualisations like the screenshot below. Soon I realised there was a lack of a proper color scheme that would assist in quickly understanding impact and importance. One way of doing this is would be by tactic.
After trying out several colour schemes I ended up with a rainbow scheme like below. Introducing, the rainbow of Tactics 😉

Most people will not know the ATT&CK matrix by heart, and this will certainly be the case in the near future with the introduction of the sub-techniques. Having a color tag will help them attribute it to a tactic and thereby providing some additional context.
By adding a color to the tagged events most graphs will become more readable and at the same time show a bit more priority in the investigation of events.
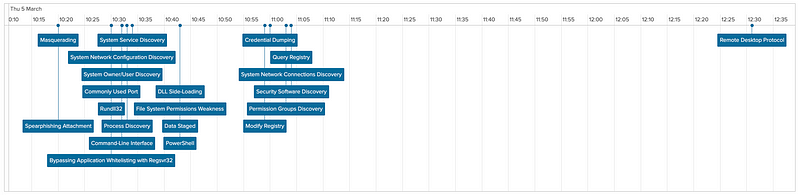
In the timeline below color tagging has been applied. By doing this it immediately adds an additional layer of information and will help focus investigations.

What you can quickly spot here is that attacks are not sequential, nor is there a normal flow from left to right across the matrix. Anyone who ever worked with the Lockheed Martin Cyber Kill Chain knows this as well. However it is interesting to track these patterns in order to be able to defend better and partially be able to predict these patterns.
Apart from dashboards, this concept can also be applied to reports, mindmaps, detection content, graphs and so on.
An overview of all colours used can be found below:

Initial Access: #d8031a
Execution: #ff2e45
Persistence: #ff4785
Privilege Escalation: #ff8041
Defense Evasion: #ffaf00
Credential Access:#ffd300
Discovery: #abc530
Lateral Movement: #01c26d
Collection: #007b84
Command and Control: #075190
Exfiltration: #86308c
Impact: #482569
Knowledge center
Other articles
Why is no one talking about maintenance in detection engineering?
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
dAWShund – framework to put a leash on naughty AWS permissions
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Exploring WinRM plugins for lateral movement
[dsm_breadcrumbs show_home_icon="off" separator_icon="K||divi||400" admin_label="Supreme Breadcrumbs" _builder_version="4.18.0" _module_preset="default" items_font="||||||||" items_text_color="rgba(255,255,255,0.6)" custom_css_main_element="color:...
Together. Secure. Today.
Stay in the loop and sign up to our newsletter

FalconForce realizes ambitions by working closely with its customers in a methodical manner, improving their security in the digital domain.
Energieweg 3
3542 DZ Utrecht
The Netherlands
FalconForce B.V.
[email protected]
(+31) 85 044 93 34
KVK 76682307
BTW NL860745314B01




